Global AppSec Amsterdam
Day 1
Remarks
A first talk about the board members and some introduction about OWASP and the question of contributing to the community and getting involved.
Explained about the membership and 50 dollar discount on owasp conferences. The wifi password was given and we’ve officially started OWASP Global AppSec AMS.
The house is built on sand: exploiting hardware glitches and side channels in perfect software -Herbert Bos
A talk about our fundament on sand, shaky and likely to crash. The exploiting of software which leads to finding zero-days for money. The focus shifts from hardware hacking to software hacking, because a lot of glitches are also to be found via Software.
Mainly through the application layer like a buffer overflow. The hype to share everything, cpu, ram, etc. Sharing may lead to sidechannels and in this case the more dangerous it may become, sharing is not caring.
Reliable Exploits, code reuse and bust. Snippets of code which can be chained together. Requires address of code and data and of course bugs!
Rowshammer vulnerability. Discovered in 2014 is a vulnerability in D-RAM that allows you to flip bits while you’re not even accessing them. You don’t know which bits but if it flips once, it will flip again. Even focused on RIDL, an exploit for INTEL CPU’s. Even the newest still has it.
We even got ourself a lego figure from the Sonatype Booth.
From left to right on the picture, there is Bram Patelski and then there’s me.

Controlled Mayhem with Cloud Native Security PipelinesJack Mannino – Ben Pick
Compares old school pipelines versus the new cloud version with k8s and new way of getting feedback through the pipeline. Like canary builds, which can get a specific amount of traffic assigned as the new updated version.
Spinnaker is a tool which is used for this. The main focus goes to kubernetes and the Jenkins x application and A little serverless with Tekton as workflow for developing.
Spinnaker vs Jenkins x, spinnaker uses the k8s api and Jenkins x also is able to use CRD’s.
So what are the security challenges and opportunities? Event driven e.g., web hooks and REST calls. The containers are not restricted, there is no hypervisor. API’s are public, think of googling a few on the internet. Create another abstraction layer, like IAM above EKS.
Don’t think a container makes your code secure. It doesn’t give you the right to produce insecure code. Understand how other layers impact your code. At creation of a pod, it uses the default account credentials. When everything is under this account, every pod has acces to each others secrets/configmaps, etc.. Limit cluster-level permissions and instead use It on namespace level.
Configmaps are public by default, so a third party option is advisable. Even Helm and Tiller are by default publicly exposed and information can be called without credentials.
Helm charts are for wiring the secrets but the secrets are publicly exposed, use hashi-vault for example to remove the exposure. Something I can completely agree on as secrets are store as base64 encoded which just basically is just a tiny little bit better as plain text.
Try to use temporarily credentials often, avoid long lived credentials. Make sure the tools cover the services you use.
This talk made me aware of situations where we definitely need to think of when we migrate to cloud-based solutions. it gave me the motivation to create list of things to think about and discuss this with the teams concerning a migration on my current assignment.
The Zest of ZAP: How scripting in our favorite tool can bridge the gap between dev teams and security – Peter Hauschulz
First of all the posture for security is stated as everybody does something until the release date seems to be delayed. The fact that security is missing in the dev cycle although every manager said they do it. So everybody is still learning and that keeps being a part of our jobs.
Also with security it is a learning curve, everybody knows it’s important but they think it’s hard or they’re scared for using/applying it. Also media made it to mysterious figures in basements hacking planes with usb key’s.
Security also has the name to look like men who just say you need to document something and nobody knows who they are. Testers already have the perspective of evaluating software, while developers have more a build perspective. So for a tester it’s seems easier to adapt to a security perspective.
How do they get involved? Create a comfortable environment where people feel good. This way they can relate to their comfort-zone and learning security at the same time. Make comparisons with subjects people like, something I can relate to as a sport instructor.
The technical part: Using the ZAP Tool for analyzing but also learning. Take one result and investigate. This is how you learn one step at a time. Zoomed in at some source code of ZAP passive scanners where creditcards regex expressions are defined.
He also points us at the script console in the ZAP tool, which understands javascript, python and some other languages. He also demonstrated it, loved the live demo!
You can create scripted tests within ZAP for evaluation, security and testing. Just like SoapUI has testing capabilities, ZAP does to but with more support. It is quite easy to create scripts and see which feedback the test has given. Zap is mostly used for security testing, where does your application crack. For you pipeline there are various options like docker ZAP where you can do baseline scanning which can be useful for integration in a pipeline.
Zest is also used for regression tests, automation, CI/CD, API testing and Integration testing besides security testing. But it can also be an excellent learning tool and step-up to the security world. A lot of software engineers don’t know what they can do with OWASP.
This also proven by the fact that this conference was quite small versus a software conference about the newest frameworks for example. Search for playground sites which are legal to scan, don’t scan NASA for instance.
Choosing the right static code analyzers based on hard data – Chris Horn
First an introduction s given, while later on the actual comparison is made. The static analysis can find realiablity, security, performance and maintance problems/risks.
There seems to be no much of information about static analysers. Static analysis improves the quality of code. Kompar is used as a example in the sheets. There was some commercial talk about Kompar. He introduced us to seven categories of analyzer properties.
It’s about commen sense IMHO that you seek out a compliant analyzer for the desired programming language used. An average analyser will find 14% of issues of the overall.
Soon Kompar is on screen for more detail and explaining. Kompar is a website or tool which helps you finding the right analyzing tool for your project and compares static code analyzers.
OWASP SAMM2 – your dynamic software security journey – Sebastien Deleersnyder
SAMM2 is the newest version of SAMM. For me SAMM was quite new as I am just beginning to discover the security world and its principles. SAMM is introduced as a Maturity model for software. Where SAMM is a principle for the whole software lifecycle. Which is a model which evolves with your company among time.
The organization can apply the SAMM model as the company suits. The maturity model is iterative, enable risk-based choices tailored for the company and must provide enough details for non-security people. The newest version is online at https://owaspsamm.org.
The SAMM model has four core functions, governance, construction, verification and operation. There are new measurement specifications released which can show you your score of security practice in the company. This can result in a bar chart which can proved an easy view on the software security currently present in the organization.
So why do they release a new version? Because the software world isn’t using waterfall method anymore as a default method. And in fact, the code guidelines actually are focused on coverage and not on quality. And in this process, it’s not the goal to be backwards compatible.
The SAMM2 model redefined the construction in two new chapters: implementation and design. The verification part is restructured for better use with the current development process. The main focus is to zoom in on the quality of the model and its content. The old version was focusing on the existence of a security model and the new is also focusing on how good is it.
Juice Shop – Björn Kimminich
Juice shop is derived from the german softladen, which are selling junk. The talk starts with a webshop where he registered himself as a customer. In that process he chooses a security question with some help by the audience. He fills his basket with some items. He fills in some gibberish as his address and tries to use a coupon code for payment.
As explained, the juice shop is a fake webshop which acts as a real webshop. At the moment there 88+ hacking challenges for the juice shop which vary in difficulty. The application has an internal score board which is aware when you successfully completed a challenge. And a new feature is the hacking instructor which helps with the easy challenges to guide you through them.
The challenges with the head button are accompanied with the hacking instructor. An working demo was given with one of the first challenges about SQL Injection. Then there was briefly mentioned how to create CTF challenges for multiple people. First create a token(flag) and that needs to be stored on a server. Multiple people take the same steps but for another server, so there can be a competition against each other. Just for fun, for with commercial use it’s too easy.
There is also a quiet mode is available for not showing notifications and links to github. The Juice shop application is completely customizable, so branding isn’t an issue if a company is giving some sort of training. It’s customizable through a yaml file.
An demo for phishing and XSS is given with an example given through sound and animation which represent the situation you’re screwed normally when you’ve clicked such a link. The Juice shop is multilingual and in a newer version also the product and challenge names are able to be translated.
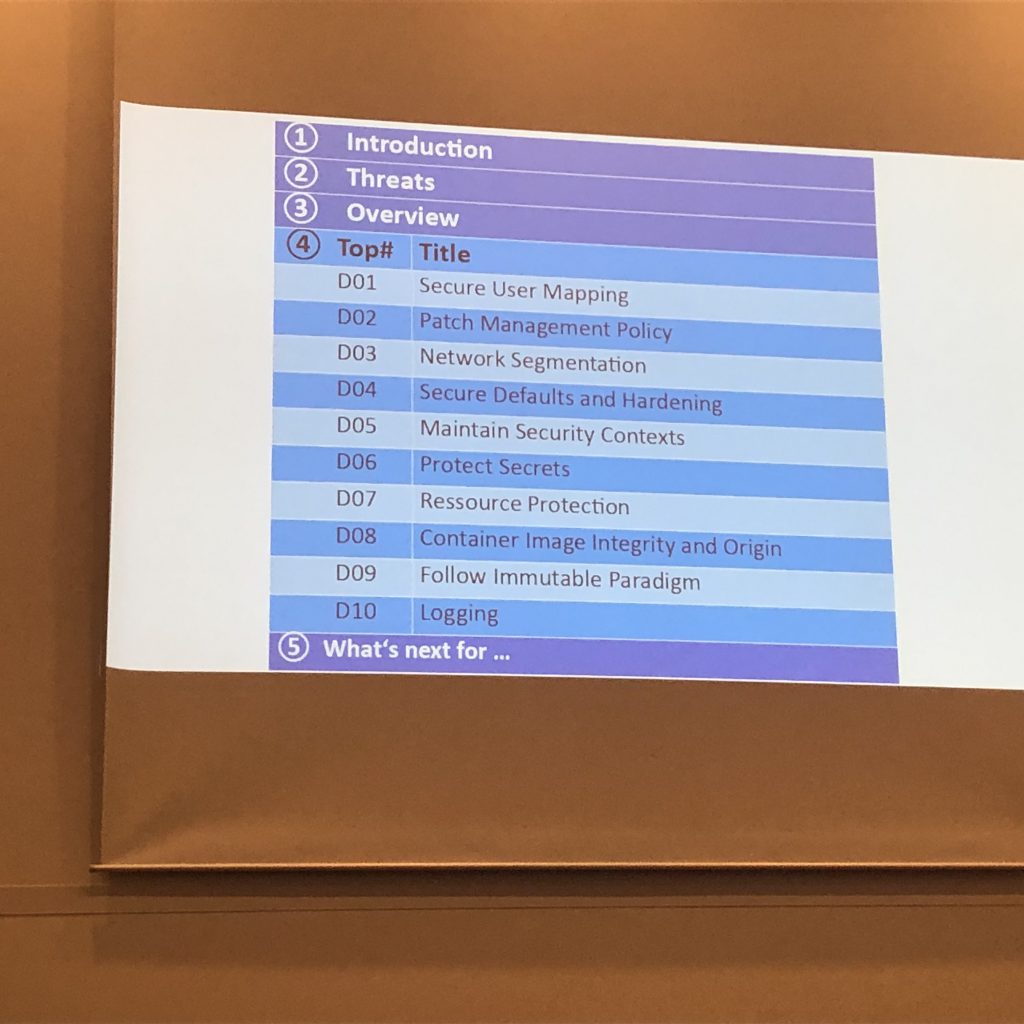
OWASP Docker top 10 – Dirk Wetter
It first starts with the sentence, understand what you’re doing! Often people say security but don’t know anything about it. What are threats to containers? Go and threat modeling, consisting of hosts, orchestration and more.
The talk was very specific and brought lots of details to the open but unfortunately time was running up and we came to number six at best. But nonetheless an interesting talk about the OWASP docker top 10 with my own developer in mind which at this point in time is really a builders perspective.
Securing the Future – Mikko Hypponen
Absolutely great talk, the moment he began, he started over the progress we’ve made and we never thought of cybercrime to be true and watch us now. The most beautiful thing is that he brought up the asbestos comparison with the IT. Some problems never seize to exist even with old software which is thought it was dead still runs on some computers.
And worth mentioning the toaster, where its data is totally useless to us but it’s valuable for its data for others. Not for yourself. Nowadays the IOT devices are spreading wide over the globe and devices are all connected, but what when they don’t connect through your WI-FI but 4g, how do you control access then.
Also, the people who didn’t grew up with IT, example he gave: An old lady which takes care of the bills of a company which pays millions of euros a month and is also looking on the very same computer at her private email or Facebook. That makes you think again.
Even the Russians and Chinese came around as he mentioned hacking, we western people don’t like getting caught but they don’t mind! And when we think about that we maybe just as bad as they are.
Finally I headed towards my hotel to do some work for coming lectures and I got inspired today as some talks had correlation with what I’m going to say.
